Identity providers
MOSTLY AI supports PingOne as an identity provider.
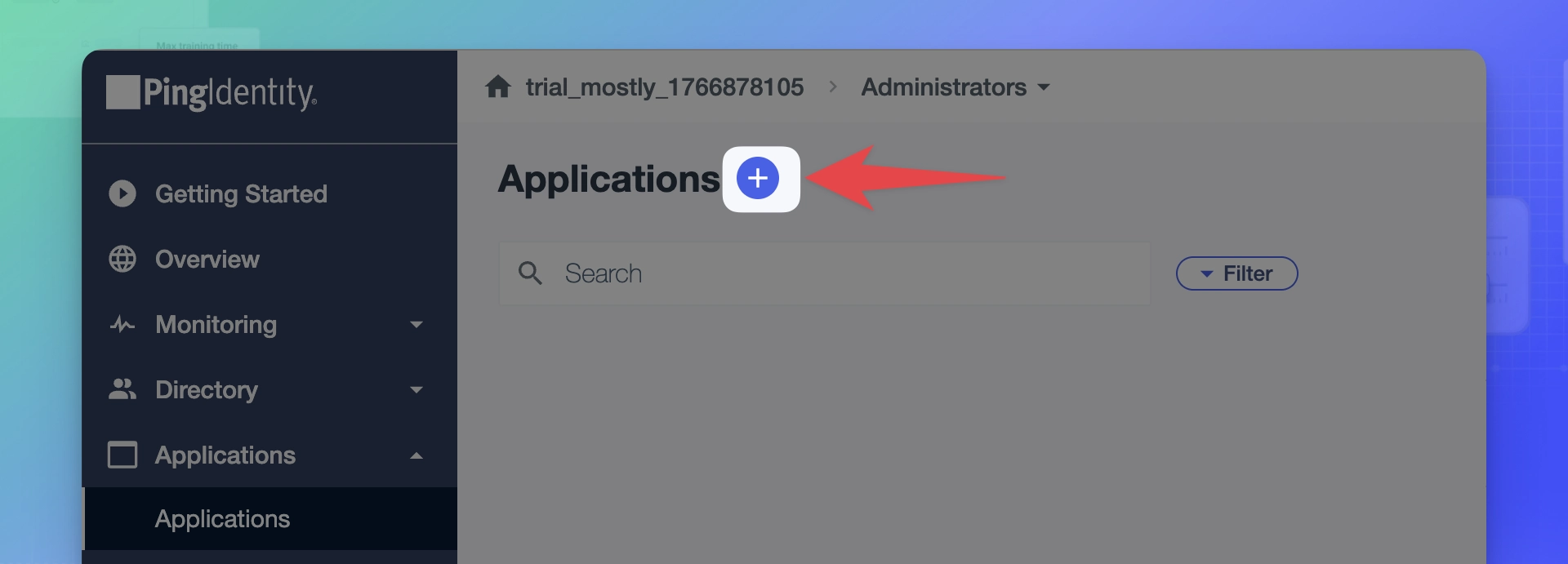
1. Create a new PingOne application
- Log in to your PingOne Admin Console.
- Click Administrators from the sidebar.
- Click Applications and then again Applications from the sidebar.
- Click on Plus icon next to the Application title.
- Enter Application Name and Description. Optionally, upload and icon.
- Select the OIDC Web App card as the application type.
- Click Save.

Result
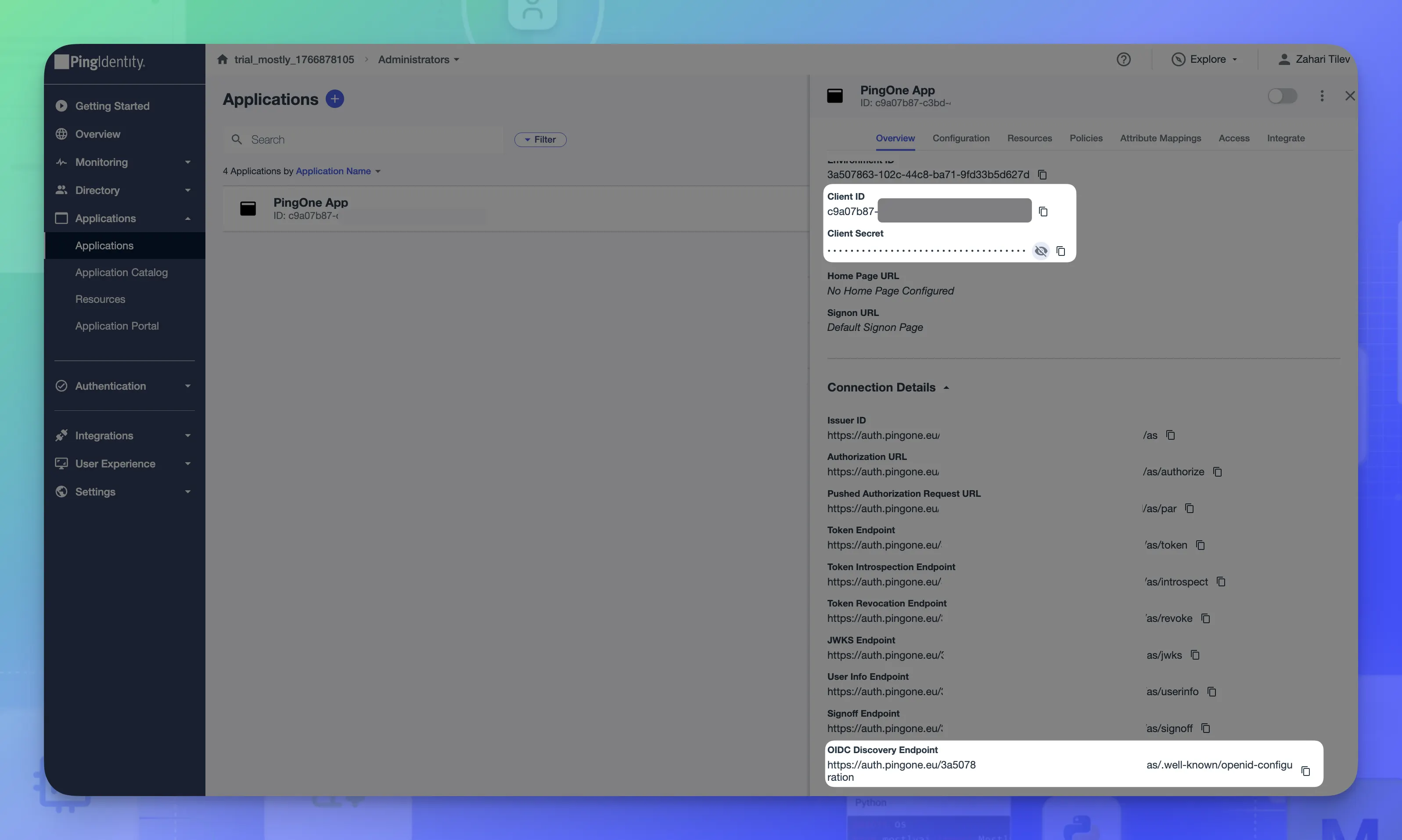
The application is created and PingOne shows its details.
What’s next
Take record of the Client ID, Client Secret, and OIDC Discovery Endpoint. All three are needed for the Keycloak configuration.
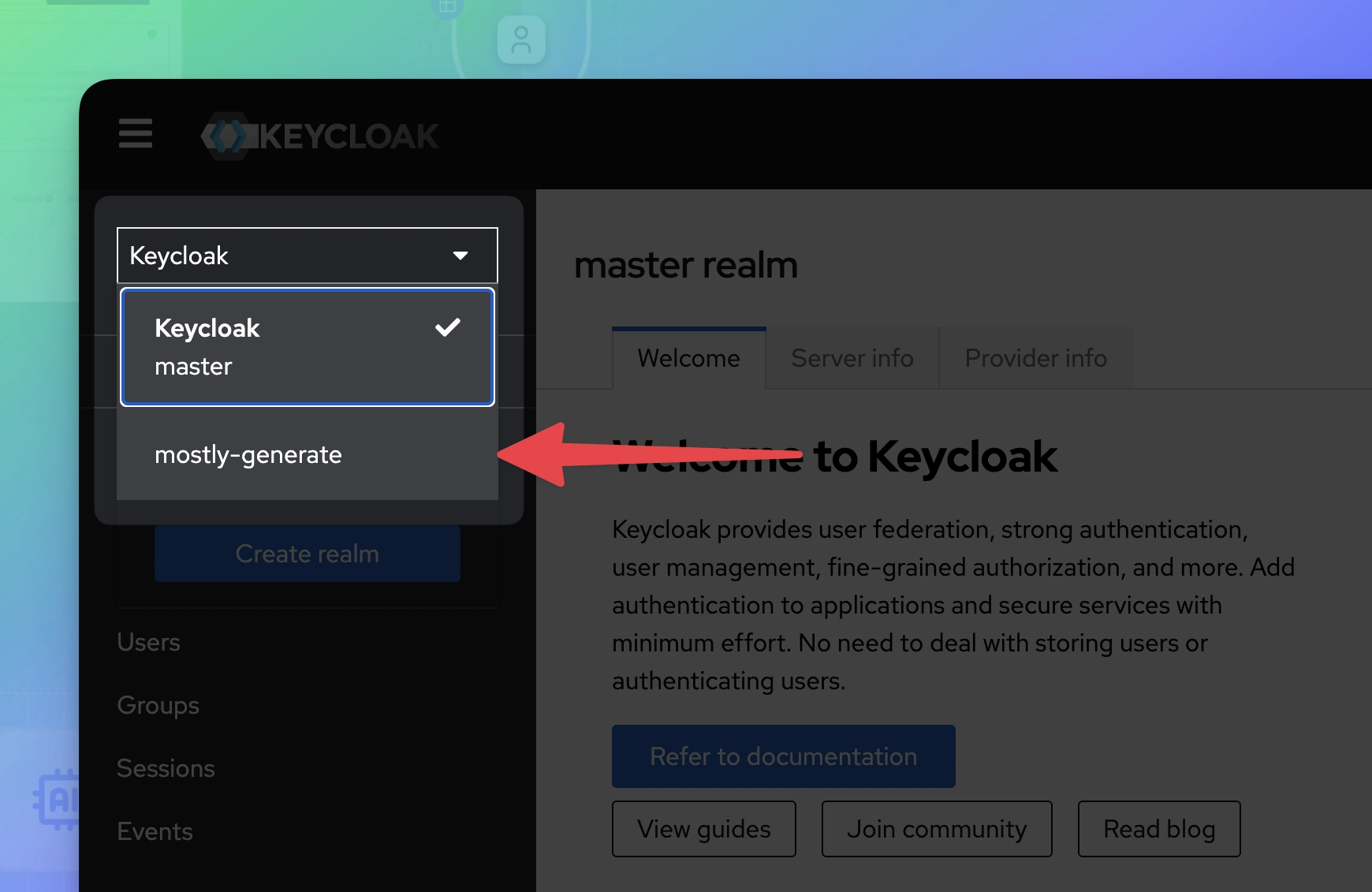
2. Create a new Keycloak identity provider
- Log in to the Keycloak Admin Console.
- From the drop-down in the upper left, select mostly-generate.
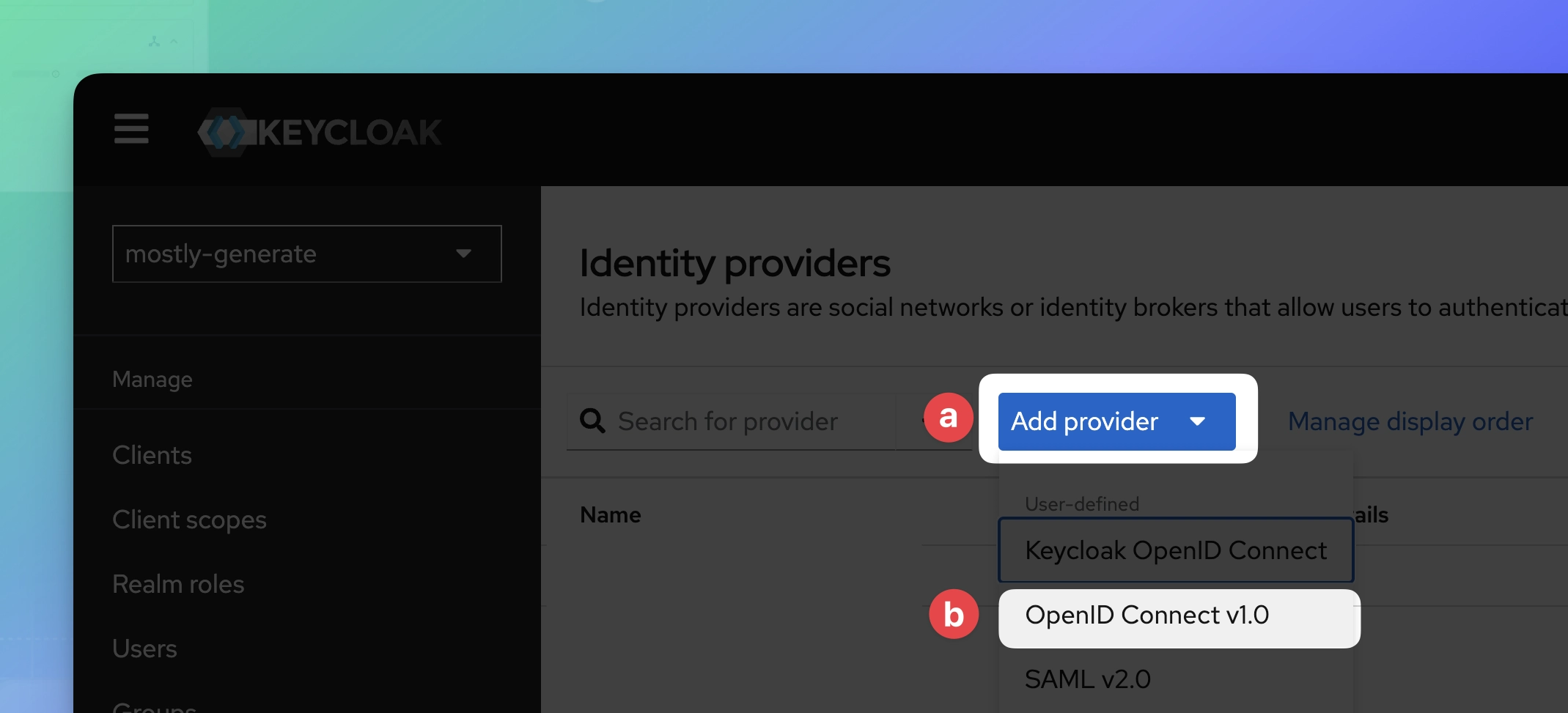
- Select Identity Providers from the sidebar.
- Click Add provider and select OpenID Connect v1.0.
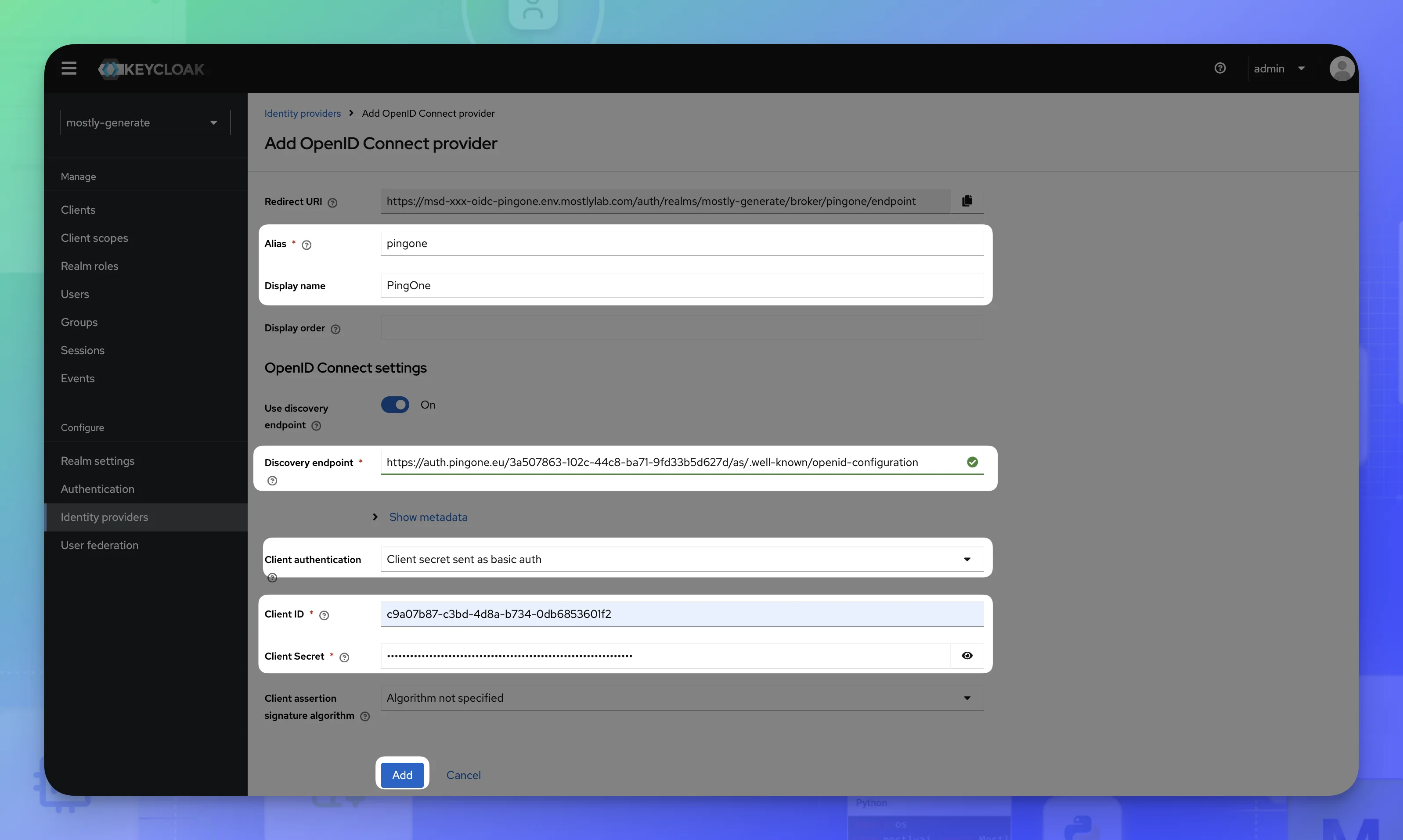
- Configure PingOne identity provider.
-
For Alias, enter
pingone. -
For Display name, enter
PingOne.💡Note the rendered Redirect URI. This will be used in the PingOne configuration.
-
For Client ID, enter the Client ID from the PingOne configuration.
-
For Client Secret, enter the Client Secret from the PingOne configuration.
-
For Discovery endpoint, enter the OIDC Discovery Endpoint from the PingOne configuration.
💡This will automatically populate the Authorization URL, Token URL, and similar fields.
-
For Client Authentication, select Client secret sent as basic auth.
💡This is the default setting for PingOne. You can change it as needed. Just make sure that the Keycloak IdP and PingOne use the same client authentication.
You can change the PingOne client authentication method under Application > Configuration > OIDC Settings > Token Auth Method.
-
Click Add.
Step result: The PingOne configuration is saved and it opens for review.
-
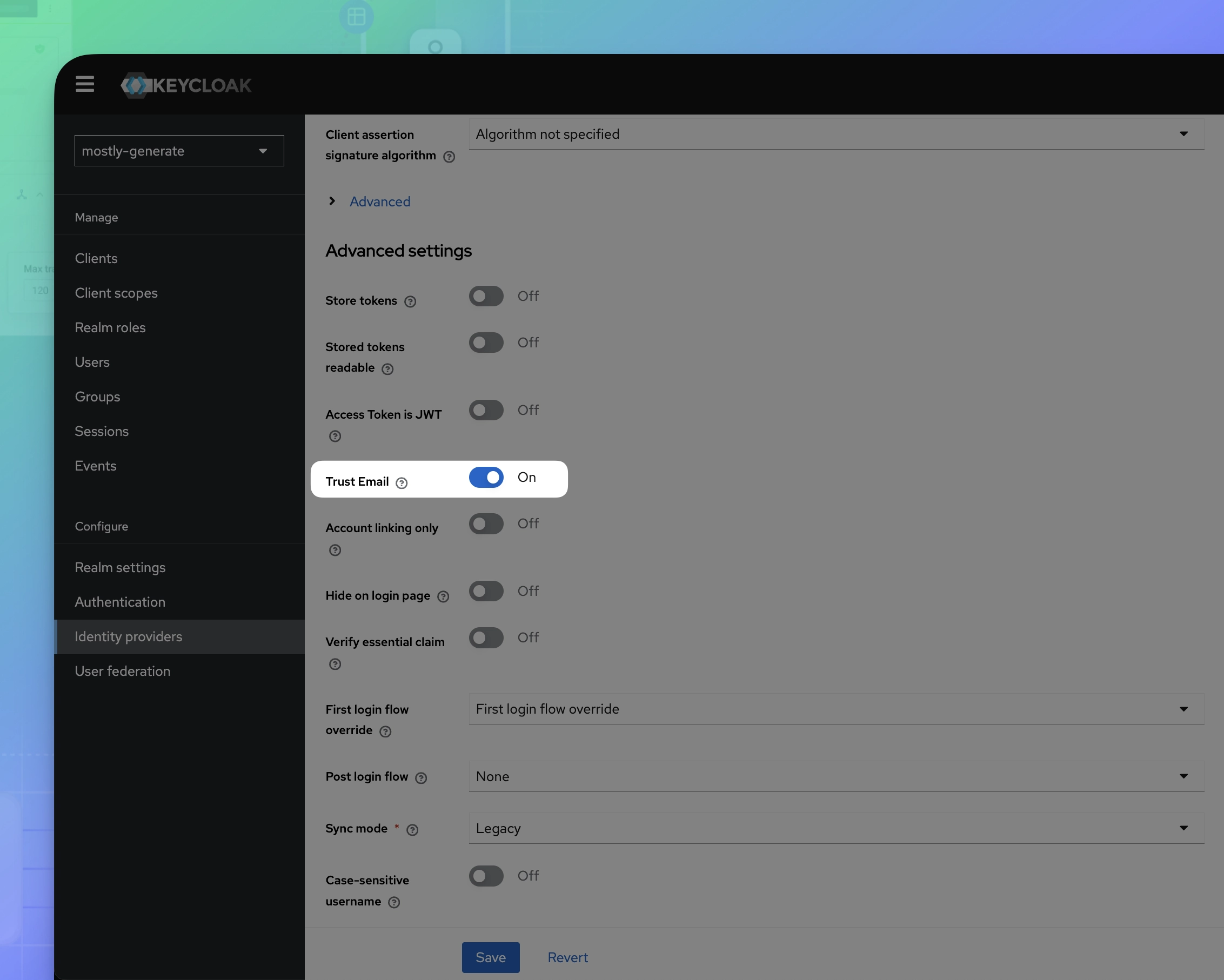
- Scroll down. Under Advanced settings, enable Trust email.
3. Configure the PingOne application
- Navigate back to Application on the PingOne Admin Console.
- Select the Configuration tab.
- Click the edit icon and configure the Token Auth Method and Signoff URL.
- Under OIDC Settings, make sure that the Token Auth Method for PingOne uses the same client authentication method as Keycloak.
- For Signoff URLs, you can set the URL to redirect to after the user logs out of the application.
For example:💡Replace:
KEYCLOAK_HOSTwith your MOSTLY AI FQDN.IDP_ALIASwith the Keycloak IdP alias.
Signoff URLhttps://<KEYCLOAK_HOST>/auth/realms/mostly-generate/broker/<IDP_ALIAS>/endpoint/logout_response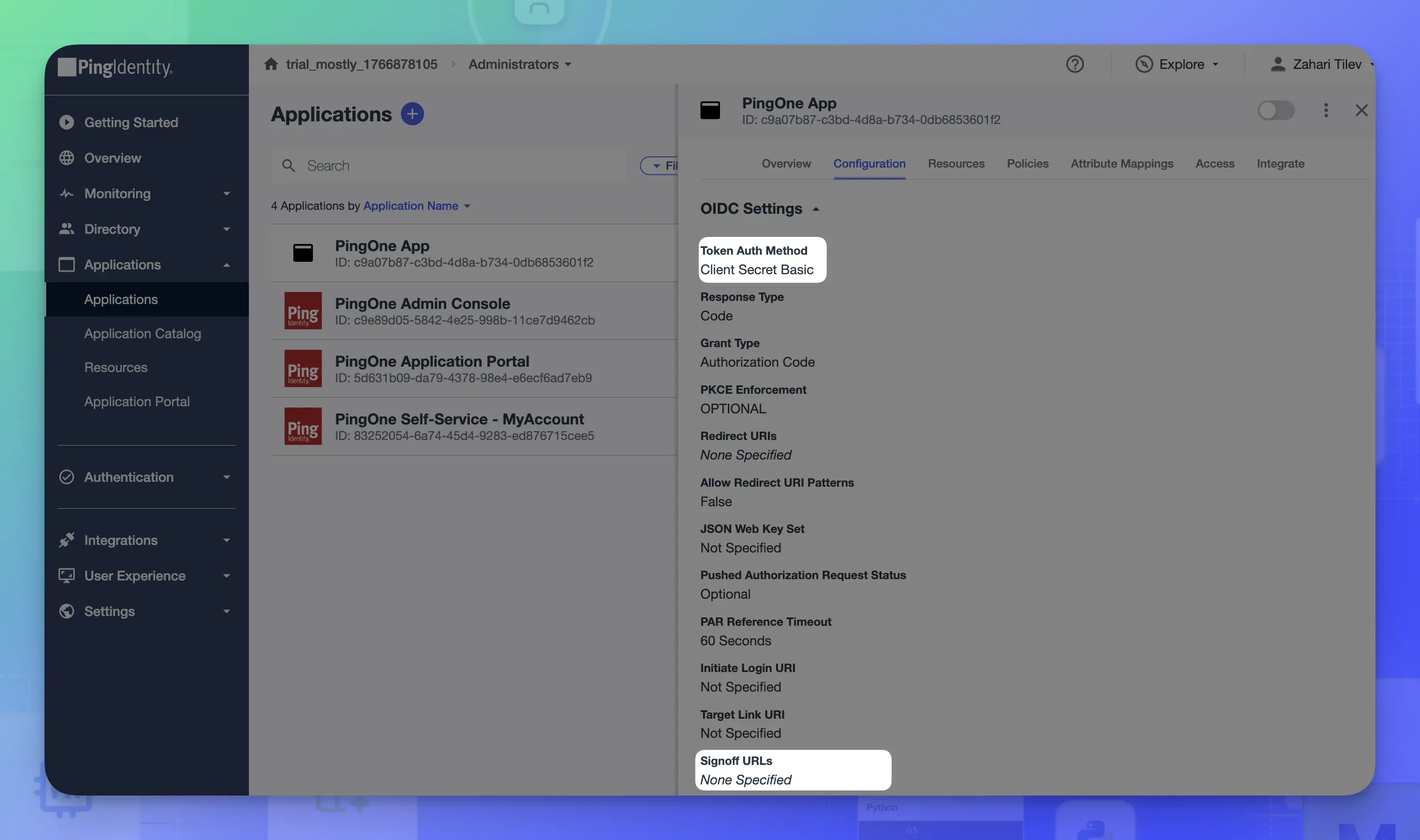
4. Configure PingOne application attribute mappings
- Navigate back to Application on the PingOne Admin Console.
- Select Attribute Mappings in the top bar.
- Click the edit icon next to Custom Attributes.
- Add the following mappings as a minimum:
sub-> User IDemail-> Email Addressgiven_name-> Given Namefamily_name-> Family Name
- Click Save.
5. Configure PingOne application scopes
- Navigate back to Application on the PingOne Admin Console.
- Select Resources in the top bar.
- Click on the Edit symbol next to Allowed Scopes.
- Add the following scopes as a minimum:
- openid
- profile
6. Configure Keycloak Identity Provider’s Attribute Mappings
-
Navigate back to the PingOne Identity Provider configuration in Keycloak.
-
Select Mappers in the top bar.
-
Click on the Add mapper button and add the following mappings as a minimum:
Name Sync Mode override Mapper Claim User Attribute Name Template Target Username Force Username Template Importer ${ALIAS}.${CLAIM.email}Local Email Force Attribute Importer emailemailFirst Name Force Attribute Importer given_namefirstNameLast Name Force Attribute Importer family_namelastName
Result
The PingOne identity provider is now configured and ready to use with MOSTLY AI.
What’s next
Your users can now use their PingOne identity to sign up and log in to your MOSTLY AI deployment by clicking the Log in with PingOne button on the landing page 🎉
You can also create organizations to control access to synthetic data resources via roles and permissions. Users can also create their own organizations to keep resources private or share them by changing their visibility to public.